Integrating Thinkst Canaries with TheHive
We've been big fans of the Thinkst platform for a while now. We may have mentioned them a time or two :) Like many others, we get a lot of mileage out of their Canaries and Canary Tokens.
We also love TheHive, as you probably already know. As we've long touted, it makes tracking incidents easy, it's reliable, and it's another well-managed open source project that we support and contribute to.
Part of our job at Recon relies on both of these tools. Our customers benefit from canaries that have been strategically placed within their environments. We're notified immediately of any suspect activity that triggers their Canaries or Canary Tokens, and that data gets triaged right away by our ever vigilant SOC analysts.
Both Thinkst and TheHive are also integrated into our NDR Training, and they've made significant impacts to our threat hunting platform and the way we train our students. Check out what we've been up to. :)
SO, WE'VE PLANTED OUR CANARIES
The Canaries can be triggered by any number of things--files opened, folders browsed, ports scanned, links clicked, credentials used, you name it.
Then those Canaries generate alerts. But where do they go?
Well, they go into a very shiny web console that the folks over at Thinkst have done an amazing job on. It's beautiful. However, we also need to be able to bring alerts from that Canary console into TheHive.
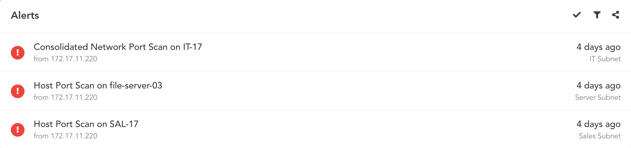
BUT WHY? WHAT DO THE ALERTS CONTAIN?
Excellent question!
Those alerts contain some important data. Data that we can turn into observables, and do some more digging on.
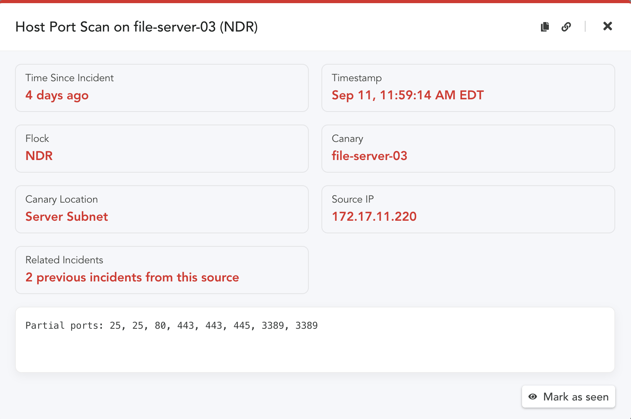
Per the above example--that source IP? Those ports? That's important information. It could be a false positive, sure. Benign scan from an IT person, sure.
It could also be an IP of a bad actor performing some reconnaissance on our network. It could also let us know that, hey, someone is scanning RDP ports and that shouldn't even be accessible. We should probably triage this in TheHive.
SO HOW DOES THE CANARY DATA GET INTO THEHIVE?
I'm so glad you asked! We've done the dirty work for you :) We developed a tool that will allow you to do just that.
The tool is aptly named canaries2thehive, and can be found here.
It's a lightweight Python 3 Flask application that listens for incoming webhooks. It can run on the same server as TheHive, or somewhere else, as long as it's reachable from the Canary console on the configured URL/IP and port.
It uses TheHive4py, which means integration with your instance of TheHive only needs the URL (which you provide in config.py) and the API key(s) (which you provide in keys.json).
config.py:
class Config(object):
HIVE_URL='http://localhost:9000'
LOG_FILE='/var/log/canaries2thehive.log'
keys.json:
{
"org1_name": "API_KEY",
"org2_name": "API_KEY",
"org3_name": "API_KEY"
}
As for integration on the Canary side, it's even easier. Create a new Generic Webhook under your Global Settings in the Canary console, and simply provide the endpoint. Clicking Add will generate a dummy alert for you to verify everything is working as expected and you will see it populate in TheHive almost instantly.
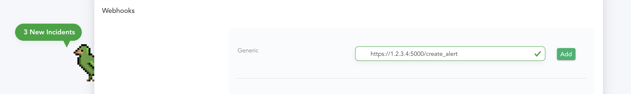
Additionally, depending on what types of Canaries you are using and what data you do or don't want to bring in, you can customize what fields you want to add as observables attached to each alert.
By default, it only adds SourceIP, CanaryIP, and CanaryName as observables, but you can add anything you want here.
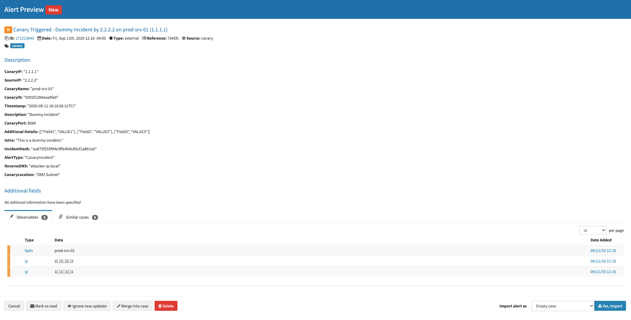
If you'll notice, you can set the TLP for each of these pieces of data as well. Once you begin running Cortex analyzers against your observables, this becomes important. You don't necessarily want to send your sensitive data to all of your configured analyzers. You likely only want to send your more sensitive data to a subset of analyzers. This way, you can ensure that your Max TLP in Cortex aligns with the TLP you are assigning to your observables.
Step by step instructions can be found in the README, so you can be up and running in no time!
WANT TO TRAIN WITH US?
We would love to train you and your team! Find more information about our offerings here, and drop us a line.
We've built comprehensively realistic attack scenarios modeled after real-world threat actors that target industries just like yours.
NDR shows teams how to take a structured approach to incident response. Additionally, it trains in effective team dynamics, such as delegation, communication, and documentation. Even the best and the brightest SOC teams can level up their soft skills while staying sharp on threat hunting.
BUT WAIT! THERE'S MORE!
If you want to learn more about Thinkst, go check out some of their offerings. Also, did you know you can deploy Canary Tokens for $FREE.99?! They've already made it so easy, but even their documentation is solid.
If you want to learn more about TheHive, their documentation is also fantastic. They recently released TheHive 4, and this tool is compatible with both 3 and 4!
We thrive on giving back to a community that has provided us with so much of what we use and rely on. Everything we've open sourced can be found in our GitHub, @ReconInfoSec.
