SOC X 2021 - A Recap
We can't start a recap post without a huge THANK YOU to the community for joining us last week and making SOC X such a success!
When we had the idea for a Professional SOC Team World Championship, we had no idea what kind of reception we would receive. The community blew us away with their excitement, which in return got us even more excited.
The event itself was a huge success and we got great feedback. People were engaged, competitive, and having fun the entire time. These are all things you hope for during any year, but especially the inaugural year of an event... in a global pandemic.
Stats
- 8 hours
- 51 teams
- 18 countries
- 243 users
- 400+ challenges
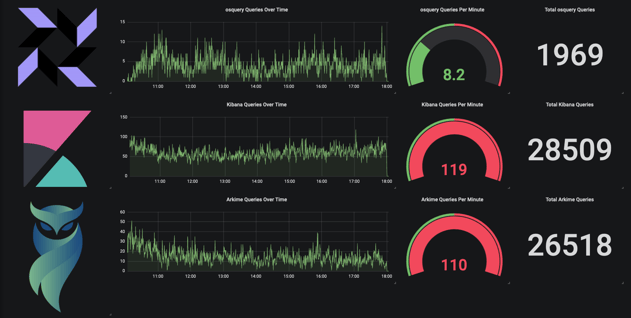
- 1,900+ osquery queries, ~8 per minute
- 26,000+ Arkime queries, ~119 per minute
- 28,000+ Kibana queries, ~110 per minute
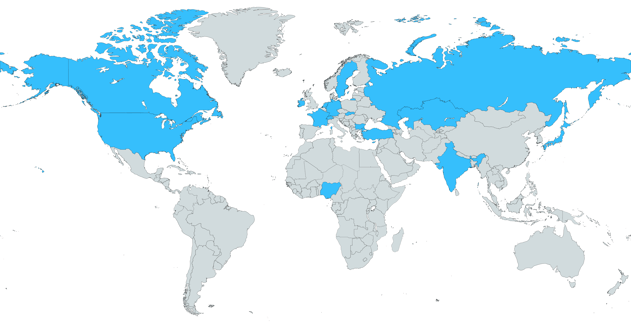
We wanted this to be a World Championship and it truly was--look at the coverage across the map! The winning team is headquartered in Canada, and 2nd and 3rd place were from the Netherlands. Some teams had a late night / early morning competing, but they powered through. 🤓
Scenarios
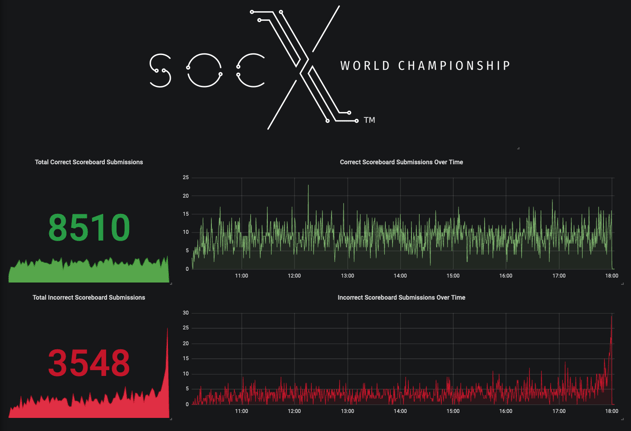
We ran 3 scenarios that made up the 400+ challenges. Out of a total possible 9190 points, the winners got 7710, leaving a few questions unanswered. We wanted to make sure there was enough content for the 8 hours, and we managed to fill it almost perfectly.
So, how difficult were the three scenarios that participants investigated during SOC X?
First off, all three scenarios for the competition were based on real world incidents involving named APT groups. Participants went head-to-head with multi-stage initial access techniques, a ransomware infection, a magecart attack, an insider threat compromise, obfuscated / encoded C2 traffic, and had to reverse simulated APT multi-stage malware (written in several languages: VBScript, PowerShell, C#, and Golang). Several months were spent developing the attacks for this competition so that the SOC teams would have to flex all of their skills.
Typically a SOC / IR team would be working one of these investigations over a week or several, but these teams had to take on three full-length intrusions in one single day!
Infrastructure
As you all know, we <3 open source tools.
We provided access to osquery (endpoint interrogation), Kibana/ELK (log aggregation/data visualization), and Arkime (full packet capture with Suricata/IDS), and teams could also use any other tools they had.
The event went off without a hitch, and the tools were completely resilient, despite the absolute pounding that these teams gave them.
Winners
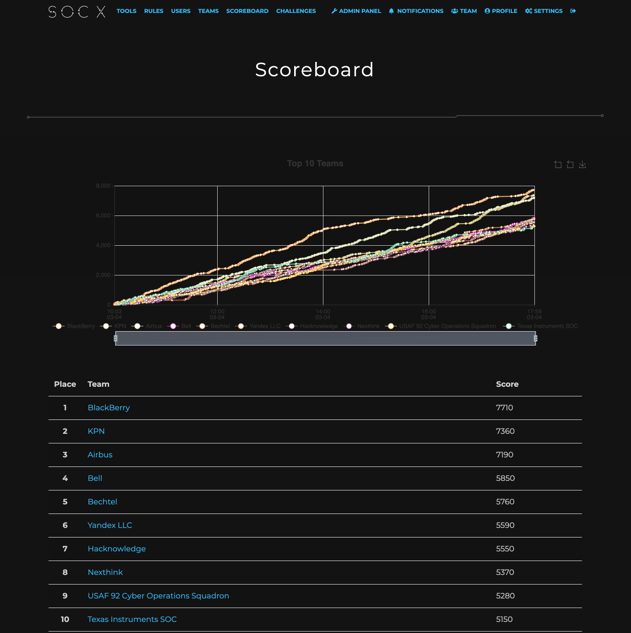
It was great watching the top 10 teams climb the scoreboard throughout the day, especially the drama between 1-3 and 4-10 at the end. I think everyone was holding their breath to see who would finish where in those last minutes.
Huge kudos to our top teams!
- 1st Place: BlackBerry
- 2nd Place: KPN
- 3rd Place: Airbus
Check out the full list of top 10 finishers in our Hall of Champions.
Thank You

We really hope you enjoyed this event as much as we did! We love giving back to the community with events like OpenSOC, so it was fun to turn OpenSOC into a professional SOC team world championship. It really is a labor of love for our team, but all the hard work is worth it when we see others as excited as we are.
Follow us on Twitter to stay up to date with the Recon team, or sign up here to keep in touch on future SOC X happenings. Also check out our training offerings if you want to see how the amazing technology behind SOC X can be used for individual or group training.
