Slacking at Security Operations
Running a Security Operations Center requires fighting a constant battle to increase analyst efficiency, speed and accuracy. Fast and effective communication coupled with automation is the only answer. So why not have both in the same platform?

GREAT FOR...
COMMUNICATION
Our Operations team has used Slack for almost a year now and the results have been nothing short of incredible. Before Slack, we communicated like most other teams, seldom and via smoke signals or email.
Since we adopted Slack, our (small) team has exchanged over 100,000 messages and 1,682 files (malware samples, malicious emails, cat memes, etc. - 1.7GB total.) While the ever-increasing rise in communication quality has been great, the benefits of using Slack far exceed this. Let's talk about the ways you can put Slack to work in a SOC.
NOTIFICATIONS
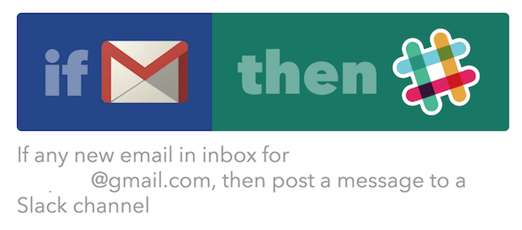
Using IFTTT and a simple Gmail inbox setup to receive alerts, you can configure any appliance or application that can send alerts via email to also drop a message into Slack.
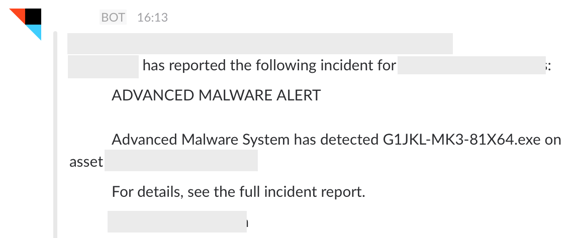
Another good use case is a User Behavior Analytics system which is only capable of sending email alerts, now those alerts can drop into Slack in real-time.
Similarly, you can utilize Slack's powerful Incoming Webhooks integration to send messages from anything that supports webhooks, including custom applications (see Automation below.)
Great for integration of...
- SIEMs sending alerts to Slack
- Ticketing Systems, notification of new tickets
- Code repos (Gitlab, Github, Atlassian, etc), notification of commits
- Wikis and updated entries
- Custom scripts that report to Slack
AUTOMATION
Now, for my favorite part, let's talk about automating security operations using Slack. My goal was to take one of the most common and tedious tasks performed by my team, and tie it directly into Slack to make it as simple as typing a message into a channel.
Building custom integrations for Slack is much easier than you might think, especially once you get the first one running. After that, it's almost as simple as copy/paste the initial framework and customize it to do something new.
To get started, it's pretty straightforward...
- Stand up a listener using Bottle which Slack will send webhooks to.
- Configure a custom Slash command in Slack. In my case I used
/blockip. - Configure the listener with the appropriate API keys/room IDs
- Profit.
Keep reading for some example integrations I have created for my own team, two of which can be found on my Github.
BLACKLIST IP ADDRESSES
The first task I tackled was blacklisting IP addresses in our perimeter firewall. To see the Python project I wrote for this, cruise over to Github. This implementation assumes you are running Palo Altos with Dynamic Blacklists, but can easily be modified to work with any API-enabled firewall.
This integration was very useful the first time an analyst on our team blocked a phishing URL for the entire network from his cell phone while at the movies with his wife. However, with great power comes great responsibility. The integration has several checks and balances in place to prevent mishaps, but ultimately it takes great care on behalf of the implementer.
Example usage would be...
/blockip block 123.123.123.123 Hosting Ransomware
/blockipis the slash commandblockis the intended action, you can alsounblockan IP123.123.123.123is the IP address we are taking action against. You can also give it a URL instead, which will get resolved to an IP address automatically.Hosting Ransomwareis the reason for the action, which will accompany the IP on the blacklist
If successful, the bot will respond to the analyst that ran the command with the following message...
IP:123.123.123.123 (URL:none) has been added to the Blacklist by <Slack Username>. Reason: Hosting Ransomware
Verify your entry here http://<internal server>/ipv4bl.txt
Had the command used a URL instead of an IP, the URL that was used would be where it says (URL:none).
QUERY VIRUSTOTAL
This one requires an API key to VirusTotal, which is free. Similar to the integration above, this one adds a new slash command to Slack to query VirusTotal for a hash or URL. See the project on Github.
This example is just as simple... Running the following command:
/virustotal 99017f6eebbac24f351415dd410d522d
Would return the following result in Slack...
Scan Results for: <Slack Username>
MD5: 99017f6eebbac24f351415dd410d522d
Detected Malicious by: 51/56
Sophos: Troj/VBHost-A
Kaspersky: Trojan.Win32.Hosts2.gen
ESET-NOD32: a variant of Win32/Qhost.Banker.BP
AegisLab: Troj.W32.VB.acgy!c
AVG: VBCrypt.AWJ
Ad-Aware: Generic.Malware.V!w.7232B058
Avast: Win32:VB-ZOF [Spy]
BitDefender: Generic.Malware.V!w.7232B058
F-Secure: Generic.Malware.V!w.7232B058
Fortinet: W32/Vb.HT!tr
McAfee: RDN/Generic Qhost
Microsoft: Trojan:Win32/Comame!gmb
Symantec: Trojan.KillAV
Scanned on: 2016-08-21 20:09:47
https://www.virustotal.com/file/52d3df0ed60c46f336c131bf2ca454f73bafdc4b04dfa2aea80746f5ba9e6d1c/analysis/1471810187/
Similarly, a query against a URL would look like...
/virustotal malware.ru
....and the result...
accept;Results for Site: http://malware.ru/
Determined Malicious by: 1/65
PhishLabs: unrated site
Sophos: unrated site
Kaspersky: phishing site
Sophos: unrated site
Scanned on: 2015-10-25 07:48:27
https://www.virustotal.com/url/a1e96fb159e1eb82c4cbb8ca342a2652ce97c16f8b214d792f9ca7262224240c/analysis/1445759307/
...making it very quick for analysts to get answers without opening another browser tab.
AND MUCH MORE...
This is really just the tip of the iceberg. I have a few more integrations that I am polishing up before I drop them on Github. Using the framework of the ones I've already published, you can build a Slack integration to do almost anything.
Soon, I'll publish a few more...
- Nmap Scanner
- Whois Query Bot
- Hash lookup tool!
