Business Email Compromise & Wire Transfer Fraud
If anyone in your organization handles financial transactions, invoices, or payroll changes over email, you're at risk of wire transfer fraud. Criminals target sophisticated social engineering attacks toward anyone that can authorize or redirect payments or financial transactions, including accountants, salespeople, payroll and HR staff, and executives. The core issue is this: email is never a trustworthy way to validate a person's identity. It is critical that your leadership and users understand this.
We’ve provided user training and guidance you can send right now to help prevent your organization from becoming a victim of wire transfer fraud.
Understand the Threat
Attackers employ a variety of tactics to trick their victims into authorizing, redirecting, or processing malicious transactions. For example, they may: Compromise an email account of someone involved in transactions
|
|
What Should I Do?
-
Get leadership buy-in. Your leadership team, such as your CFO, needs to understand the threat of wire transfer fraud over email. Send them this guidance from the FBI and the training videos below so they understand the risks and what controls your organization needs to put in place. Let them know that you can implement technical controls to help mitigate the risk, but that the organization requires additional policy, procedures, and training.
-
Implement policy. All transactions and modification requests should be logged (for example, in a spreadsheet or form), including the source of the request and how it was validated. Transactions over a certain amount or should require additional validation steps, including an out-of-band conversation over a trusted medium, such as an outbound call to a known-good phone number. Store ACH/wire information in a secure location that requires authentication (such as Box.com); send links to the information rather than emailing the information directly.
-
Train and enforce. Make your users aware of your organization’s new policy and train them on the threat. See "For Your Users" below for an example of what that email might look like.
- Check your email filters. Email filters serve as a first line of defense. Implement email filters to help block malicious messages with common fraud-related keywords from untrusted sources and newly registered domains. However, understand that email filters cannot completely stop the threat and may even block or delay legitimate messages while still allowing malicious ones.
-
Implement email banners. Configure inbound emails to remind users of the policy when the email contents likely contain keywords related to financial transactions. Configure outbound emails to append a disclaimer asserting to your customers and vendors that you will never modify bank account or payment instructions over email.
-
Enforce MFA. All email accounts should be protected by multi-factor authentication (MFA). Failure to implement and consistently enforce MFA puts your organization at an extreme risk of business email compromise.
For Your Users
Here is an example of what you can send your users that handle financial transactions. Modify it to match your policy and instructions!
|
Subject: Wire Transfer Fraud Over Email If you handle financial transactions, invoices, or payroll changes over email, then you are at risk of wire transfer fraud. Criminals target sophisticated social engineering attacks toward anyone that can authorize or redirect financial transactions, including accountants, salespeople, payroll and HR staff, and executives. The core issue is this: email is never a trustworthy way to validate a person's identity. The Policy: Everyone is expected to exercise caution when handling financial transactions over email, including but not limited to processing invoices, wire transfer instructions, banking information, and payroll instructions. All wires and ACHs should be tracked on the Wire/ACH Verification Tracking Sheet, including the source of the information (invoice, transfer request form, etc) and how it was validated (name and contact #). Transactions meeting the following criteria always require you to confirm the validity of the request over a trusted medium other than email:
Training: Everyone is required to review the following guidance from the FBI and watch the three training videos below: |

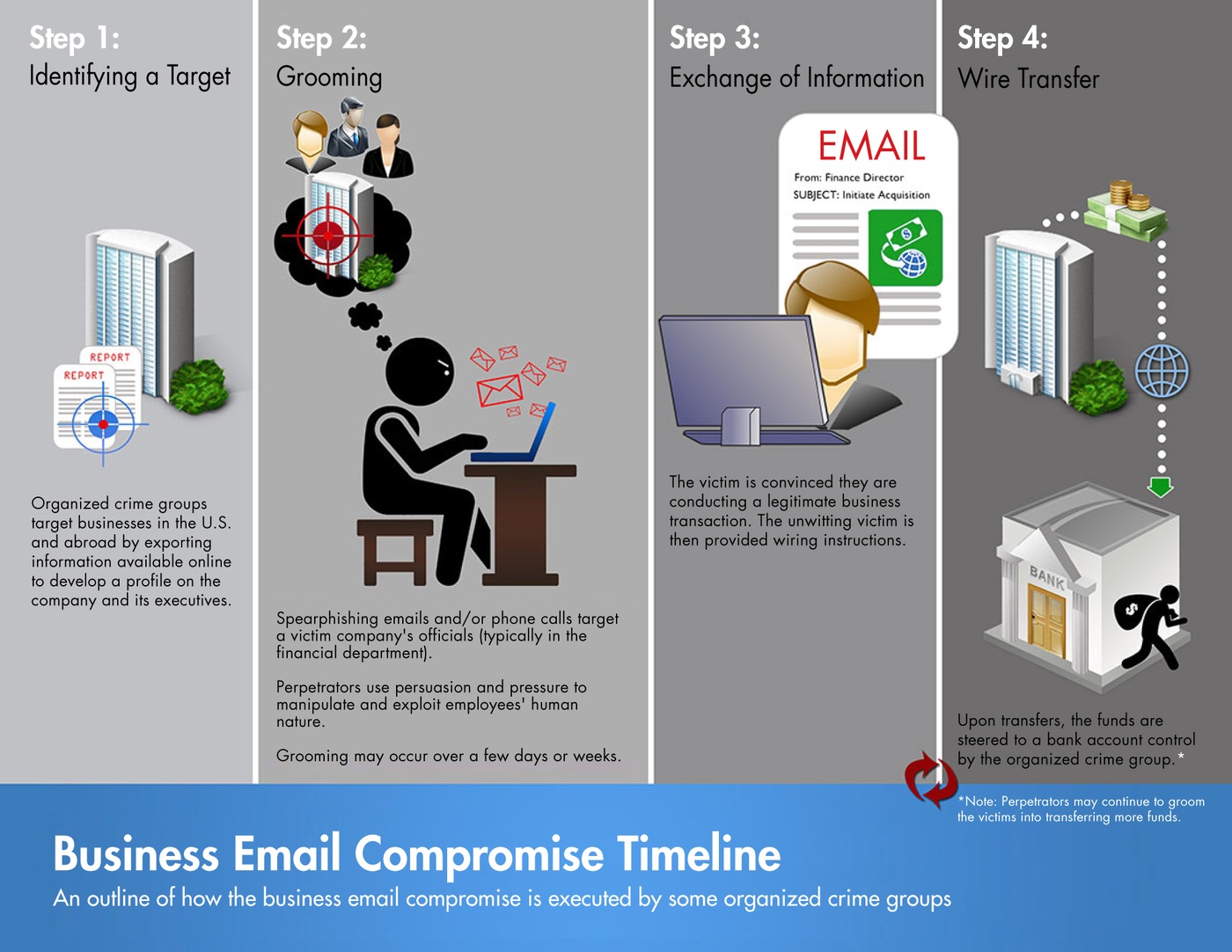 source: fbi.gov
source: fbi.gov
