Advanced Email Protection: Detection Techniques in Action
Hopefully you have read all about why we are excited to be offering Advanced Email Protection (AEP) to our customers. If you have not, check out that blog here. In this post we wanted to take a deeper dive into a few common phish attacks and the detection rules we use in Sublime Security to identify them so we can automatically quarantine them for customers.
Spear Phishing
When attackers use spear phishing as a method for credential harvesting, they frequently attempt to spoof common vendors that have a standard email template that users expect to contain a URL that should redirect them to a sign in portal. These could be things like a DocuSign invite, a shared file in SharePoint, OneDrive, or Google Docs, or even just an account security notice. Using image analysis and Optical Character Recognition (OCR) on the contents of emails, Sublime is able to identify references to those common vendors in an email. It compares the vendors found in the images and text of the email to the actual sender and can even analyze any links in the email and flag on malicious content. This allows analysts to see that a malicious actor is pretending to be Microsoft or DocuSign and automatically quarantine those emails before users are able to interact with the email.




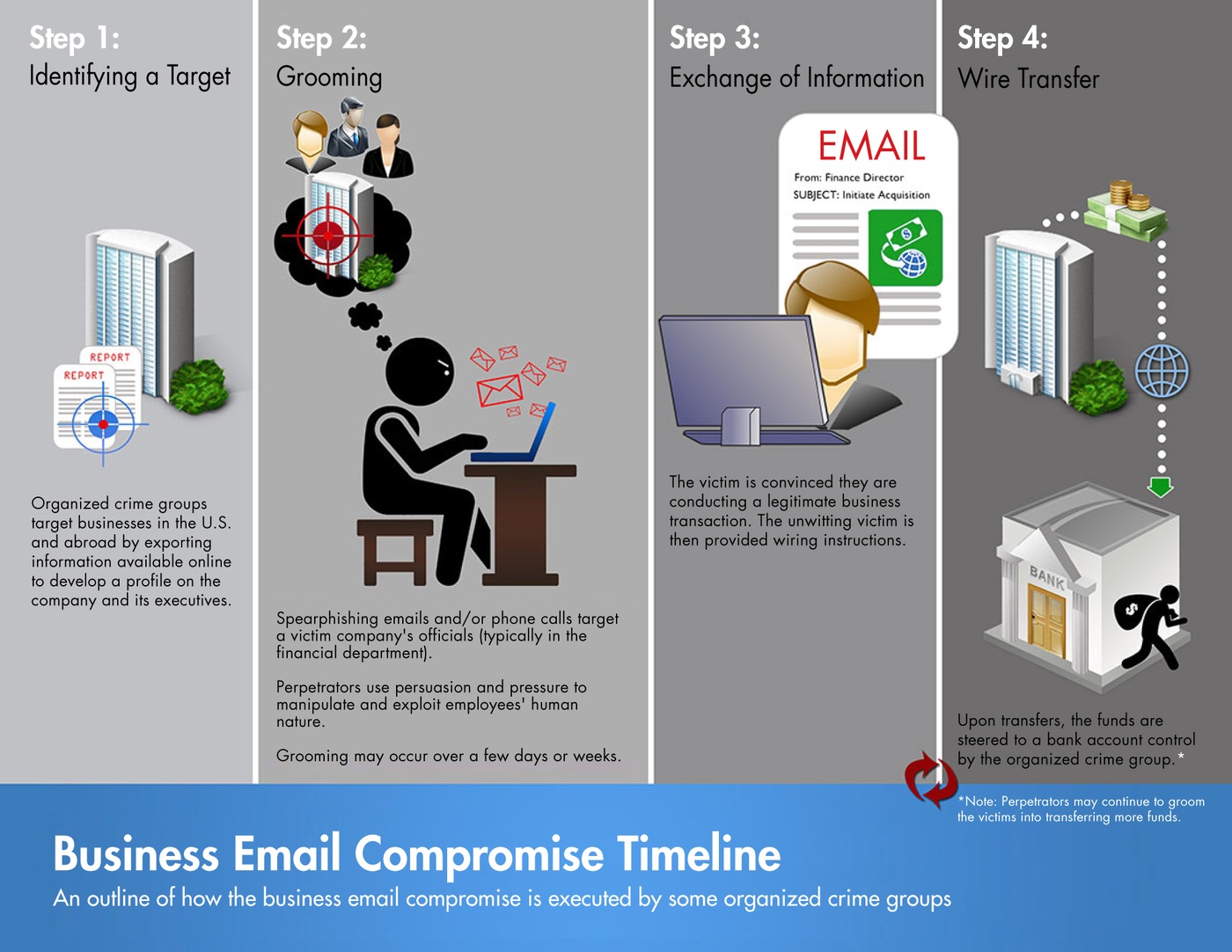
Wire Transfer Fraud
If you are not familiar with how attackers use phishing to conduct Wire Transfer Fraud, check out our blog here. These attacks are frequently successful because attackers set up new email domains that look very similar to your customer or vendor’s domain. At first glance, your employees may not notice the domain has changed. Email security gateways struggle to catch these types of phishing emails because the domains don’t have a malicious reputation and the emails themselves don’t normally include any malicious URLs, attachments, or QR codes. The analysts at Recon are able to create detections around these Sublime Insights:
- First-time Sender or First Time Sender Domain: Sublime recognizes the first time your organization receives an email from a new external email account or domain. By itself this is not malicious but when combined with additional insights it can be a concern.
- Levenshtein Distance of Sender Domain: The Levenshtein distance is the number of changes that need to be made to take one string to another, for example the Levenshtein distance between acme.com and acme-us.com is three. A low Levenshtein distance between a domain that regularly sends emails to your organization and a new sender domain can be a sign of a malicious actor using a look-a-like domain.
- Newly Registered Sender Domain: When a new business is established, organizations often purchase those domains weeks to months before they start using them to send emails. When malicious actors use look-a-like domains, they frequently register those domains just a few days before sending their first emails to the organizations they are targeting.
- ACH info from New Sender: Just like with a First-time sender domain, Sublime is able to recognize electronic money transfer information in emails and will flag when this information is coming from a new sender. Alone this is not necessarily malicious, but in combination with other concerning features about an email it can be a sign of wire transfer fraud attempts.
Employee Impersonation
Malicious actors often try to take advantage of trusted relationships when targeting users. They accomplish this by trying to spoof other employees in your organization. Two common forms of impersonation are malicious actors pretending to be someone on your executive leadership team requesting users to take immediate action and malicious actors pretending to be employees contacting human resources for payroll changes. Sublime is able to recognize these impersonation attempts from external senders and use machine learning to analyze the content of the email for language that is associated with fraud or urgent requests.

These are just a few examples that demonstrate how powerful Sublime’s detection capabilities are. Our analysts at Recon take full advantage of these different insights when creating new detections for our customers to ensure we are stopping the newest email threats before they impact your users. Bad actors will always have a human element available to adjust their tactics. With the combination of the outstanding technology from Sublime and Reon InfoSec’s strengths in detection engineering and security operations you have an outstanding solution working to elevate your security.
If you’re interested in exploring Advanced Email Protection (AEP) further, we offer a comprehensive 30-day look-back proof of concept (POC). In a short call we can scope the effort and without any impact on your existing email solutions, our team will review the past 30 days of your emails. We will provide a detailed report highlighting any malicious emails that bypassed your current security measures, identify the most targeted individuals in your organization, and analyze the types of attacks that have been most prevalent. Even organizations with existing protections typically see an average of one malicious email per mailbox. As attackers rapidly adapt, it’s crucial to stay ahead with solutions that move even faster. Contact us today to enhance your email security.