Mapping Adversary Emulation Plans
The Center for Threat-Informed Defense at MITRE recently released their Adversary Emulation Plans Library on Github.
This is exciting news for anyone who conducts adversary emulation (something we do extensively as part of our Network Defense Range engagements) or studies adversary actions (which is fairly applicable to most everyone in Information Security).
These adversary emulation plans outline the actual actions of an adversarial attack, down to the commands executed. And better yet, presribes a thoughtful framework and schema for describing the procedures executed. Each procedure is mapped to applicable MITRE ATT&CK technique(s), which further provides the ability to analyze defenseive posture against a specific adversary.
Here is a short snippet of the fin6 emulation plan:
# Phase 1: Discovery
- id: e44a39ce-0651-3ddd-8f05-f83aa2ffd657
name: Enumerate AD person objects
description: Find all person objects and output the results to a text file.
tactic: discovery
technique:
attack_id: T1087.002
name: "Account Discovery: Domain Account"
cti_source: https://www.fireeye.com/blog/threat-research/2019/04/pick-six-intercepting-a-fin6-intrusion.html
procedure_group: procedure_discovery
procedure_step: "2.1"
platforms:
windows:
cmd:
command: |
'adfind.exe -f (objectcategory=person) > ad_users.txt'
payload: adfind.exe
...
This is a goldmine of information about adversary behaviors and gives us a way to automate this information into our SOC processes. Additionally, having common designs and frameworks to communicate adversary behavior, can event clarify discussions about defensive capabilities.
Use Case
In a previous post, we oulined how we use MITRE ATT&CK Navigator to visualize our defenseive posture. Specifically...
we can quickly respond to a new adversarial TTP and focus on improving our coverage
ATT&CK Navigator has an awesome feature which allows us to dynamically build "calculated" layers from other, existing layers. So, if we can build a Navigator layer from the Adversary Emulation Plan, and compare it against our real-time defensive capability map, we can quickly, and visually, identify where our gaps may exist in identifying this particular adversary.
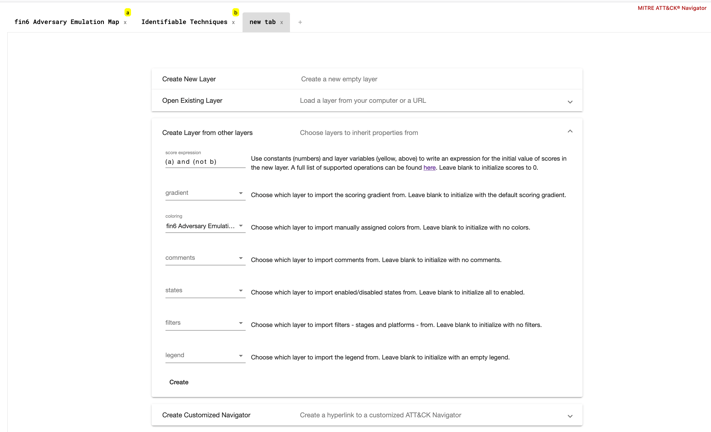
At the time of writing, layer images exist for the emulation plans, but no actual layers exist. So, like any good haxors, we wrote something. Enter: adversary-emulation-map, a Python script which reads emulation plans and generates an ATT&CK Navigator layer based on the techniques recorded in the plan of your choosing.
Here is the output of the "fin6" plan: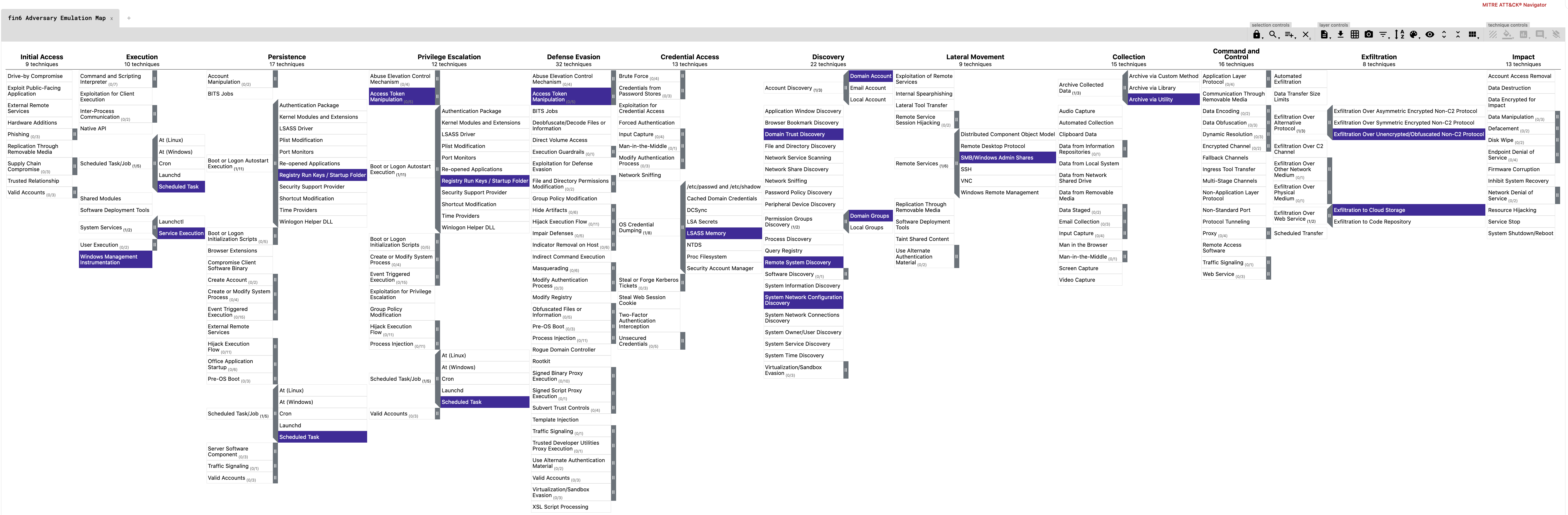
Now, we can build a calculated layer against both our Data Sources map and our Identifiable Techniques map to quickly visualize the techniques we are best suited to utilize.
Final Thoughts
If you check out this post on the OpenSOC blog you will notice that we love yaml and automation. The contributors to the Adversary Emulation Library were thoughtful enough to build out a JSON schema which we can use in an IDE of our choosing (in this case: VS Code) to assist in building additional emulation plans in the same, awesome format:
"yaml.schemas": {
"./.plans/format_schema.json": "*/Emulation_Plan/*.yaml"
}
Check out the source code for the Adversary Emulation Mapping tool on Github: https://github.com/ReconInfoSec/adversary-emulation-map
